- | 10:00 am
CrowdStrike could have a European-size data problem on its hands
While CrowdStrike already faces criticism for bricking 8.5 million PCs worldwide, data-protection experts say it’s possible the company also breached data-protection laws.
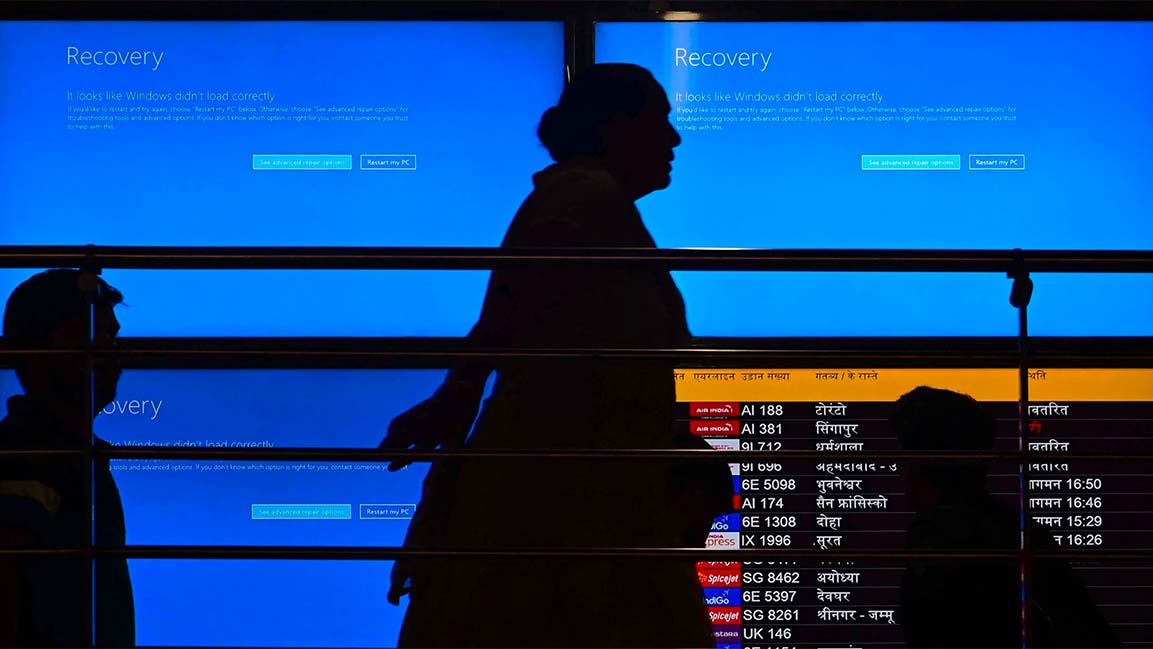
CrowdStrike’s massive malfunction on Friday sent 8.5 million Windows computers into blue screen of death (BSOD) mode and affected everything from hospitals and airlines to banks and subways. (Little wonder the company’s share price has tanked 18% in the past five days.)
One estimate puts the cost of the outage at trillions of dollars. Even now, after the company pushed out an update to fix the problem, CrowdStrike is far from being out of the woods.
Alongside the inevitable class action lawsuits CrowdStrike will likely face in the United States for the disruption its erroneous update caused, it could be on the hook in the U.K. and Europe for potential breaches of the General Data Protection Regulation (GDPR), which imposes limits on how companies can collect data without user consent. Fines under the GDPR can be up to 4% of a company’s global revenue.
“No one disputes that huge amounts of personal data have been affected in the CrowdStrike incident, and the questions that will be asked in the coming months will focus on what harm was caused to the individuals in question and who—if anyone—will be liable,” says Jon Baines, senior data-protection specialist at Mishcon de Reya, a London law firm.
In theory, Baines suggests, it’s possible for organizations affected by the CrowdStrike outage to have breached data-protection rules by preventing people from accessing their personal data. Ordinarily, companies have to report any breaches of the GDPR. But whether those organizations would have to report those issues in this instance is less certain.
On X (formerly Twitter), data experts are debating where responsibility lies—and how CrowdStrike has to make good. Compliance and technology lawyer Jonathan Armstrong posted “that data doesn’t need to be exfiltrated for it to be reportable under GDPR. If you can’t access data for a period of time that can be reportable too.” Others, including data-protection expert Pat Walshe suggested that CrowdStrike’s claims the issue was not a “security incident” are wrong, and that GDPR may be possible to be applied. A third data-protection expert, Daragh O Briain, said he reported it as a breach of article 32 of the GDPR, which covers the security of processing personal data.
On paper, the CrowdStrike incident has caused what in the terms of the GDPR could be classed as a “personal data breach.” That’s where there has been “a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data transmitted, stored or otherwise processed,” according to the wording of the regulation. That loss of access is why some data-protection experts believe CrowdStrike or its clients could be on the hook. (CrowdStrike did not respond to Fast Company’s request for comment.)
But it can be difficult to determine whether a breach has occurred in the first place. “Some will argue that there is clearly a ‘personal data breach’ here because of the fallout effect, others may not consider the definition’s threshold to have been met at the causal end,” the data protection and digital privacy expert Rowenna Fielding wrote on LinkedIn.
Baines, for his part, falls in the latter camp alongside Fielding. “In my view, a temporary lack of access to personal data does not constitute a ‘personal data breach’ that requires notification to the [U.K.’s Information Commissioner’s Office, or] ICO,” he says. He’s clear that doesn’t mean that an incident like CrowdStrike’s doesn’t infringe on the idea in the GDPR of keeping data secure. But rather that it wouldn’t require self-reporting to the ICO.
But that’s the problem: The letter of the law and the spirit of the law are two different things. “The purpose and intent of the GDPR is to protect people’s rights and freedoms,” says Fielding. “To the extent that processing of personal data has been disrupted by the incident and resulted in harms and/or rights are affected, there is a ‘GDPR issue’—but not necessarily an infringement.”
And it’s unclear whether the company would itself be liable under the law. “CrowdStrike was neither a controller nor a processor of the personal data which was rendered inaccessible in the incident,” argues Stewart Duffy, legal director at global cybersecurity company CyXcel, a consultancy within the U.K. law firm Weightmans.
Instead, Duffy argues, CrowdStrike was a third-party supplier of a “technical measure” on which controllers and processors relied. “Where those entities are within the scope of the E.U. or U.K. GDPR, any breach of those regulations will be within the reach of the relevant supervisory authority, with the possibility of sanctions,” says Duffy. “CrowdStrike’s liability will be contractual—to the controllers and processors with whom it contracted directly.”